The cloud you’ll be known by
You hardly ever notice it, but your valuable company data constantly moves to more places than ever—from your desktop to your phone to a tablet to your watch to any device in your life. Amazing for productivity, but possibly devastating if you don’t have a repeatable, end-to-end approach to manage and operate your cloud environment. And remember, it should also maintain and improve business performance, agility and innovation at every data transfer and destination.
The risks of a breach, error or missed detail in security and compliance go well beyond the often-quoted $8 million-plus price tag of a security breach. You’re on the hook for any regulations you’ve missed. (Think HIPAA in the United States, or GDPR if you do business in Europe. More on that later) But that’s just the start. The reputational damage of breaches, regulatory miss-fires or leaks of information can be monumentally (and immeasurably) catastrophic. How much did the crypto-mining breach of Tesla cost a few years ago? Or the more recent phishing-to-ransomware attack on Cisco?
Trouble is, there is no shape to the cloud. While its protean nature is one of the unique strengths of cloud computing, it’s also one of the things that makes it devilishly difficult to secure. What’s needed is a framework that allows you to assess, remediate and then build and operationalize the best practices to secure your cloud environment—without business disruption. Let’s have a look at how Onix approaches these things to help you sketch out your security picture.
To secure your cloud, you need to understand:
- What information assets do you need to protect?
- What are the risks that may lead to financial or reputational loss if these assets are compromised and exploited?
- How well are the cloud security controls you currently use protecting those assets?
Seems pretty straightforward—until you start to break it down.
First of all, you’re already operating with security measures. Presumably, you’ve already identified a number of ongoing security issues. We’ve found most organizations have a vague strategy or general approach to security, but few have a really clear and solid security strategy and operations plan in place—whether you’re operating in the Google Cloud Platform (GCP) or elsewhere. And then there are those regulations we mentioned earlier. Compliance with evolving HIPAA, SOC, NIST, ISO and GDPR rules are a recurring issue.
And don’t forget preparing for and passing audits.
You may not have the expert personnel, resources or time to properly assess the security and risks to your cloud environment, but you know—or at least you suspect—that they exist, right? That’s where the uncertainty lies. So, let’s talk about how to clarify and address all of them.
Start with the outcomes you want in mind
Before taking the first step on a journey, you need to know which direction you’re going. So before you take any action, be clear on what priority business outcomes you seek. Of course you want to identify which security practices aren’t effective, such as weak security strategy and operations. We’ve already covered that as the overarching goal. But beyond that, which of the following do you seek to achieve?
- Stay ahead of compliance challenges and changes in HIPAA, PCI, NIST, CIS and GDP, for instance?
- Demonstrate to customers and stakeholders the commitment to secure and protect valuable assets?
- Pass technology and business audits with flying colors?
- Identify potential security issues and develop a prioritized approach for remediation?
- Minimize risk to financial assets, customer data or intellectual property?
- Position your organization for rapid evolution of governance strategy and management changes?
The natural answer is “YES, please! All of the above.” But the question we’re asking is more nuanced. We want to establish your unique roadmap to:
- Gain objective insight into cloud security right now.
- Select and make operational improvements for security and risk management.
- Implement preventive controls to remediate issues in real time.
- Pass those audits and meet compliance and regulatory requirements.
A cloud security framework to fit your unique needs
To deliver all this, Onix has developed our SecGov Framework. It’s that repeatable, end-to-end approach that enables you to manage and operate cloud environments while maintaining, and improving, business performance, agility and innovation securely and efficiently.
The SecGov Framework is our starting point to quickly and thoroughly expose and address security and governance issues, plan the short-term steps to remediate these issues and craft a long-term plan to operate and manage the cloud securely using best practice standards (typically as part of a compliance framework). The framework includes:
- Risk assessments.
- Cloud security findings and technical remediation.
- Security strategy, foundations and operations.
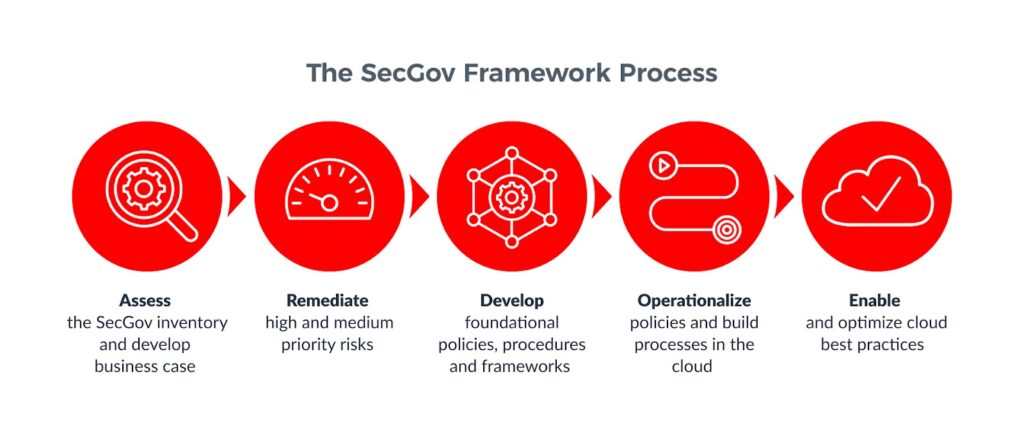
The Onix SecGov Framework in action
A healthcare use case
So what does this repeatable process deliver in reality? There’s no better place to look for that than reality itself. And among the harshest, the most stringent use cases for security and governance may be the healthcare field. Even more than finance, the security of healthcare information is critical. Breaches can decimate your reputation; drain your resources through civil, regulatory and business costs; and bring about the end of even the largest healthcare system through non-financial penalties. Working with healthcare companies, the Onix SecGov Framework has delivered within the Google Cloud Platform, but the general use cases apply generally as well.
For migrating healthcare companies, the SecGov Framework has provided a secure, step-by-step blueprint to the Google Cloud Platform. Let’s look at how the five steps applied here.
Assess: Create a Data Classification Matrix
Too many companies don’t know what it is they want to protect. Through reviews and discovery sessions with healthcare company leaders, technical stakeholders and subject-matter experts, we first develop a clear GCP Cloud Inventory Document and provide a Gap Analysis of your current situation.
Remediate: Solve immediate gaps
Using CloudGuard scanning, Onix creates a risk assessment document on which to base a prioritization of actions needed for remediation.
Develop: Define Governance Policies and Procedures
Document HIPAA and GDPR Technical Controls, HIPAA Policies and procedures relative to the GCP Foundation (logging, access management, encryption, etc.) to GCP Best Practices.
Operationalize: Follow the Cloud Adoption Roadmap
Through documentation of necessary governance policies and procedures and close collaboration, Onix provides a Cloud Adoption Roadmap and supporting documentation specific to the company’s needs.
Enable: Stand it up in the GCP Landing Zone
For a company migrating to the GCP, we create a GCP Landing Zone Architectural Design and documentation, deploy and validate it using infrastructure as code (IaC) practices. This includes Organization hierarchy, IAM Policies, Network, Storage, Computing, Logging and Monitoring.
Assessment is the first step: Start your risk assessment
Whether you’re experiencing security gaps now and looking for the best way to close them, or you don’t know where your gaps are, a Rapid Risk Assessment is a low-effort way to pinpoint your current SecGov inventory and priorities.









