Traditionally, organizations have used service account keys as a secure mode to grant access to cloud-based resources. However, as cloud security concerns continue to rise, Workload Identity Federation (WIF) has emerged as a more secure and contemporary solution for cloud access.
What is Workload Identity Federation, and why is it critical for modern enterprises? Let’s discuss.
Understanding Workload Identity Federation
Workload Identity Federation (WIF) is a method that provides secure access for external applications (or workloads) to authenticate their cloud services without requiring credentials such as passwords and API keys. As an alternative to service account keys, it uses short-term tokens provided by trusted identity providers (IDPs) such as MS Azure, AWS, or OpenID Connect-compatible systems.
For instance, in a Google Cloud environment, external applications and workloads – whether on-premises or on other cloud platforms – can access Google Cloud resources without requiring service account keys.
With the implementation of WIF, every application (or workload) needs to prove its identity to the IDP to receive the token and access cloud services. WIF also overcomes the limitations of service account keys, such as stolen credentials and management overload.
Next, let’s look at some of the benefits of WIF as compared to service account keys.
3 advantages of Workload Identity Federation
Here are 3 advantages of Workload Identity Federation over traditional service account keys:
-
Improved security
Service account keys (like user passwords) are more long-lasting, thus making them more vulnerable to an accidental leak or cyberattack. Insecure key management can also compromise secure access to critical cloud resources.
On the other hand, WIF implements short-term tokens, which are less likely to be leaked or compromised. This technique also eliminates the need to store critical keys in any codebase or configuration file. -
Lower management burden
Service account keys require enterprises to regularly rotate and store them to avoid any misuse, which can be a resource-intensive process. On the other hand, a WIF simplifies cloud access with short-term tokens (issued by the external IDP). This lowers the cost and hassle of storing access keys. -
Improved scalability and flexibility
When compared to the traditional service account keys, the WIF approach allows organizations to easily scale up their cloud infrastructure. This makes it more suitable to add new users, applications, workloads, and resources to the cloud. Besides scalability, they find WIF more flexible when it comes to accessing cloud resources.
Service account keys vs Workload Identity Federation – comparative analysis
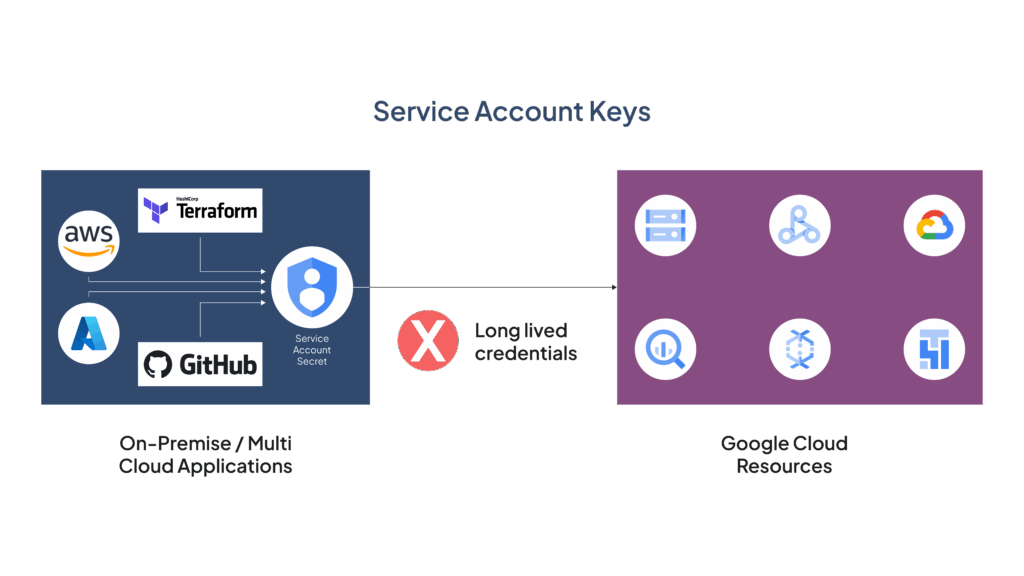
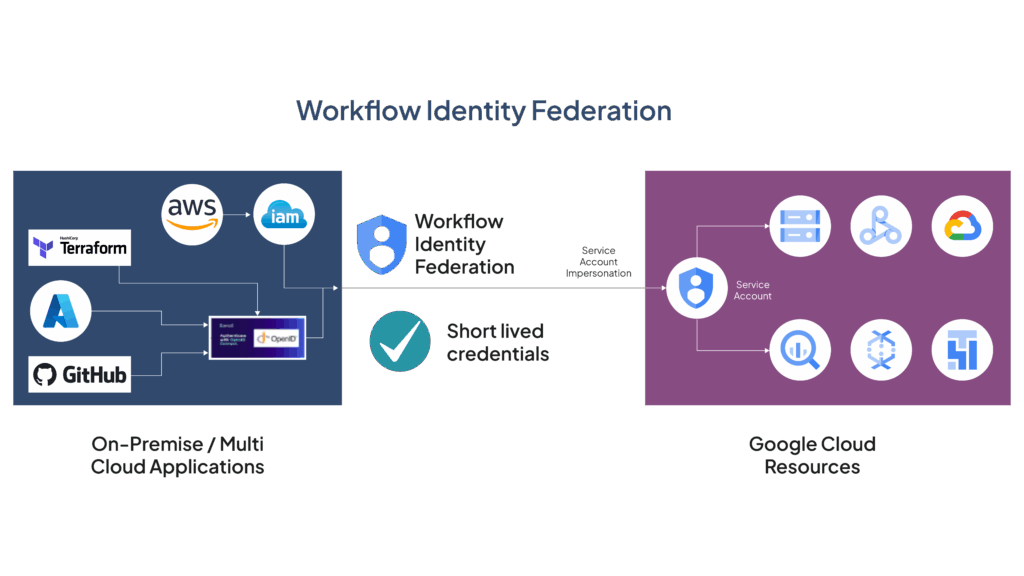
The following table provides a feature-wise comparative analysis of service account keys and Workload Identity Federation.
| Feature | Service account keys | Workload Identity Federation |
|---|---|---|
| Lifespan of credentials | Long-term usage – until revoked or changed | Short-term usage – through tokens |
| Security risk | High risk – due to possible leakage of keys and strict storage requirements | Low risk due to the use of short-term tokens |
| Key management | Requires manual management of account keys and secure storage | Does not require long-term key management and secure storage |
| Access control | Identity access management requires key roles to access account keys | Fine-grained access control using scoped tokens |
| Multi-cloud compatibility | Limited to Google Cloud services | Cloud agnostic – works with multiple cloud service providers |
| Usage in hybrid cloud environments | Difficult as it requires key management in multiple locations | Easier access from on-premises and multi-cloud environments |
| Data governance and compliance | Challenging – to meet compliance requirements without efficient key management | Simplified – to meet compliance with ephemeral tokens |
| Use case | Legacy applications with simple access requirements | For modern, scalable, and secure cloud applications |
Next, let’s discuss how enterprises can implement a Workload Identity Federation system for secure access.
How to implement WIF
Here’s a 6-step process to trigger a Dataproc cluster through GitHub Actions by using WIF:
- Create a WIF pool.
- Create a WIF provider (GIT).
- Impersonate a service account with WIF.
- Add roles to the service account.
- Create GitHub actions using a YAML file.
- Run the GitHub Actions workflow.
Let’s look at each of these steps in detail.
-
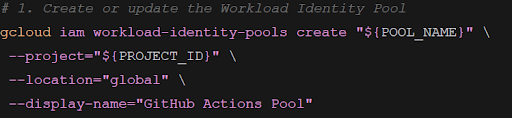
Create a WIF pool.
Here’s how to create a WIF pool named “GitHub Actions Pool”.
-
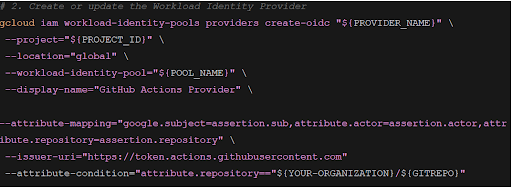
Create a GIT pool provider for WIF.
The next step is to define a GIT pool provider for the workload identity system.
-
Create a service account and bind it to the WIF pool.
Next, create the service account and bind it to the WIF pool. Additionally, define the IAM policy bindings for the WIF system.
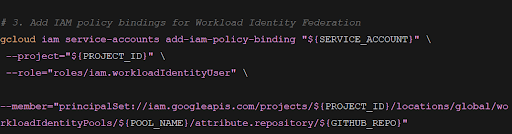
-
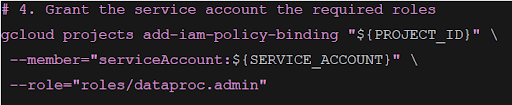
Add the authorized roles to the service account.
Add the required roles (for example, a Dataproc administrator) to the newly created service account.
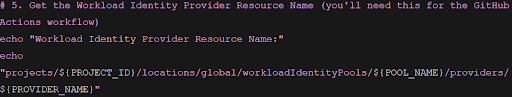
Note down the WIF resource details for the GitHub Actions workflow.
-
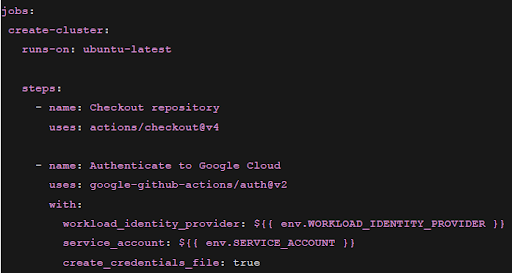
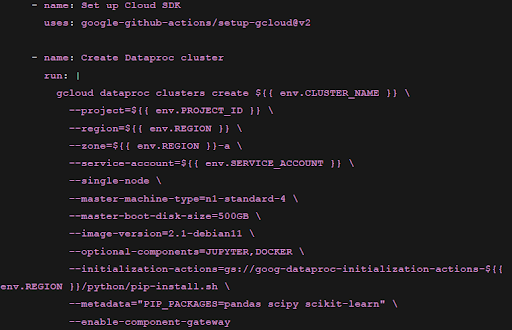
Create the GitHub Workflow Action file.
The next step is to use WIF to create a Dataproc cluster as shown below.
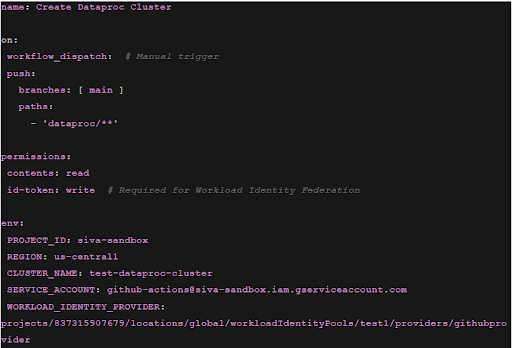
-
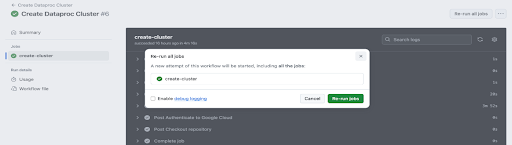
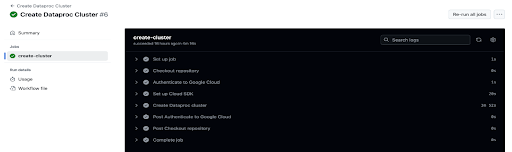
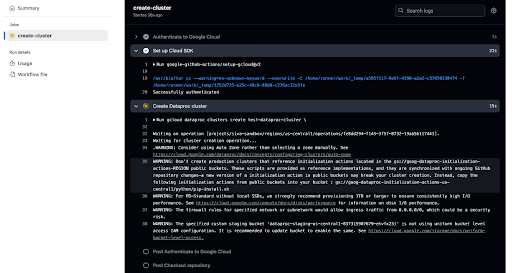
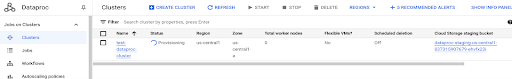
Run the GitHub Actions workflow.
The final step in WIF implementation is to run the GitHub Actions workflow (as illustrated below).
Conclusion
With the development of Workload Identity Federation (WIF), enterprises now have a secure and scalable approach to provide access to their cloud-hosted resources. By switching from static service account keys to WIF, enterprises can significantly improve their cloud security posture and integrate seamlessly with hybrid and multi-cloud environments.
As a long-standing partner for the Google Cloud platform (GCP), Onix delivers the best of Google’s cloud technology for the benefit of its global clientele. Our cloud experts are prepared to help you transition to GCP-enabled Workload Identity Federation for secure access.
Contact us to know more about our cloud solutions.
References:
What is Workload Identity Federation?
Google Cloud Security Tips #4 – Workload Identity Federation









